Currently Unavailable Please Try Again Later Gatehub
Tracing my stolen funds stored without due care by GateHub

I wanted to write this post to lay out the follow-on actions I decided to take on the incident I recently experienced with GateHub. This is an ongoing matter with them. Just over USD 103,000 (iv Jan 2018) worth of my investments disappeared in their apparent "100% safe" intendance (17,900 XRP and ix.25 ETH, converted to 32,000 XRP before it was stolen).
After speaking with regulators, cyber crime and financial law-breaking specialists in my network I came to the conclusion the authorities practise non have enough resources to look later on the fiddling guys. Sure, the large cases are looked at, but unless your case adds upwards to many thousands or millions, or if in that location are many victims of a similar issue coming forward, so sadly chances are the authorities will never get to it.
What I have as well found is that there is no service on offer — unless I just don't know of any —that an individual can call-on to investigate cyber or fiscal crime breaches or incidents. Seems the specialist companies that exercise be are only interested in the large corporate cases or where there are hundreds of thousands or millions involved. You can meet why; the usual price / benefit challenge…
I besides wanted to put this out there to speak-up most the ongoing 'political party' the cyber criminals are enjoying across the cryptocurrencies space and expose how they operate and and then others tin see the dangers, just more than importantly give those companies that do perform investigations a bit more info than but maxim: "my funds were stolen, can you help?".
This volition also flush out the complete lack of oversight the wallet providers and exchanges have on financial criminal offence on their platforms, never mind the bad cyber security defences of some.
So, here we go. If you lot recollect I've got things wrong, let me know — happy to listen and change class.
My goals:
- Follow the trail of the stolen funds to see where it ended up, and who has / had it!
- Try and figure out the assail vector and vulnerability, and who was at error.
First Transaction — consolidated funds; preparing for the theft
The outset transaction is where the hacker was in my GateHub business relationship and exchanged my ETH for XRP on the GateHub platform.
My XRP accost is 'rPiGtVmyJzHfqZkXVPZUVuHvZDnQjcRr6T'.
This is merely changing one currency, i.e. USD for another currency, i.e. GBP. Purely a change of one cryptocurrency for another cryptocurrency but within the same account effectively.
Paradigm ane is the transaction details on GateHub, and Image 2 is where it hitting the Ripple blockchain. Image iii is a Bithomp query which provides an indication where the receiving address is registered and provides more than detail.
On GateHub (Wallet / Exchange / Ripple Gateway):

On Ripple (Blockchain):

On Bithomp (Ripple Account Explorer):
In this case, the receiving address is registered in GateHub's proper noun, which is fine, as that is where one cryptocurrency was exchanged for some other cryptocurrency within the same account on GateHub.

2d Transaction — bodily theft; funds transferred out of my business relationship
The 2d transaction is where the hacker sent my XRP* from the GateHub platform (from within my business relationship) to an accost registered by a user on the Poloniex platform.
Poloniex is some other cryptocurrency exchange. These exchanges are like traditional stock exchanges, it is where currencies are traded against each other.
* The XRP I endemic, plus the newly XRP he/she got from exchanging my ETH.
Then really what this appears like is the cryptocurrency (my coin!) was transferred to someone who has an XRP account with Poloniex.
On GateHub:

On Ripple (Blockchain):

On Bithomp (Ripple Business relationship Explorer):
The highlighted address in Paradigm five and the Image 6 is the address of the hacker (rHdNRDdqB1hSEHmPvCdnJvLU7W7oQsBGVq) to where the stolen funds were sent to, and the very outset accost exterior of GateHub that received my cryptocurrency.
The ruby circled transaction is the i in question — see the amount? You lot can likewise see the address that sent that amount is my wallet accost. Date and time marshal — that'due south my money!
The interesting thing hither is the person last used this address on 20 September 2017.
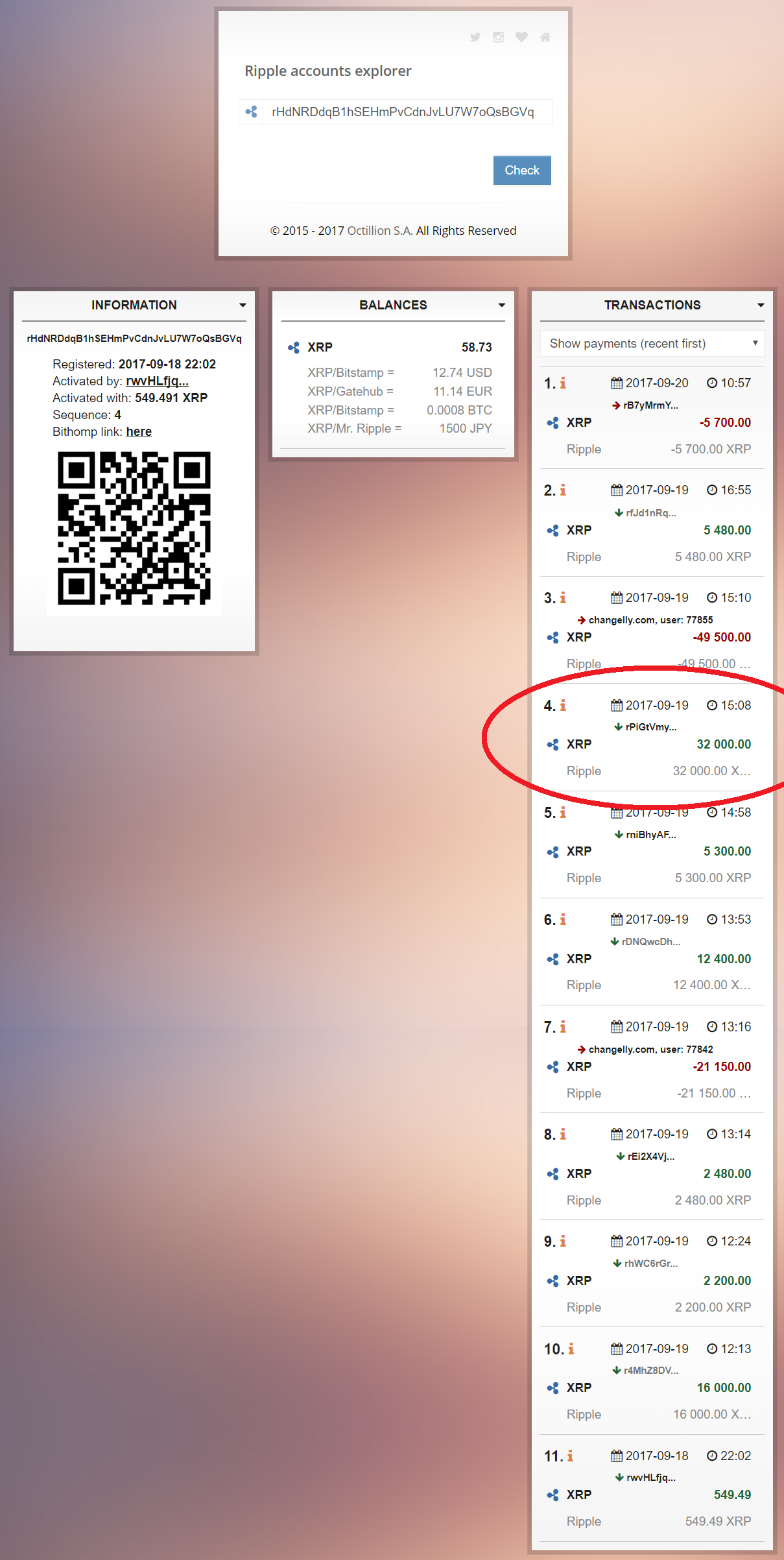
How do I know it is Poloniex? Yous will notice the address starting with 'rHd' was activated by a person with address starting with 'rwv' (refer 'Activated by:' Image half dozen).
When you and so follow that trail — run across Image 7 below — yous clearly run across the address 'rwv' was activated past Poloniex.

What'due south more than interesting — if I understand this correctly — is that the person is notwithstanding very much active on Poloniex. By the looks of things the final time on 20 October. O, did nosotros say cyber criminals are all the same running riot on the very platforms nosotros trade on everyday…?
What happened to my funds
And then at present that we take seen in that location is still activity, question is what happened to my funds and who has it.
Back to Paradigm 6. Per Bithomp the address 'rHd' (of the hacker) transferred funds (49,500 XRP) to a Changelly* XRP account (encounter 'changelly.com, user: 77855'). If you look at the history of the account, that is the amount that includes my stolen funds. The address associated with that Changelly account is 'rPujGTiw6nKmMvAiUT6UjpFxT9QrDn9kJP'. This accost is Changelly's XRP accost.
* Changelly is another wallet and exchange. I contacted them for more than information and asked the question if they know the user '77855' on their platform. No response at the time of writing this. Surely the code 'user: 77855' must mean something?
Let's take stock
Going dorsum to my goals, on one — so far we know where the stolen funds went to and we know Changelly user 77855 has/had it.
We tin't encounter what happened to the funds from Changelly onwards, as the history I have access to via Bithomp doesn't go dorsum equally far as that — as I said, the hacker'due south address is withal agile on Changelly as nosotros speak…Bithomp only keep the last 200 transaction public.
Who is this thief, can he/she exist identified?
The place nosotros start at is the accost that first received the stolen funds (come across above), that was 'rHdNRDdqB1hSEHmPvCdnJvLU7W7oQsBGVq'.
Google didn't yield any results on that accost.
There is no point in searching Google for address 'rPujGTiw6nKmMvAiUT6UjpFxT9QrDn9kJP' equally that is Changelly's XRP address.
So really we are at the mercy of Changelly to come up with who the user 77855 is. The expectation is KYC/AML would have been done, right? Then they ought to know who the person is…
Even though I contacted Changelly, I am not belongings my breath as they tin just cite customer confidentiality and say they can't release the details.
Goal 2 — Identify set on vector and who was at fault
I know for a fact my network, devices, email or credentials were not compromised.
The reason I desire to place this is to arroyo GateHub to concur them accountable if they were hacked or due to a software malfunction.
Access Logs:
I accessed my GateHub account and found an access log. I could see the post-obit IP address accessed my business relationship via Chrome which do not belong to me on Sep 19, 2017 at 16:07:07 PM — the aforementioned twenty-four hour period the assault took place.
2602:ffc8:1:c:9cbd:c2a6:f420:3bd7 (U.s.a. IP)
I don't use any VPN software.
However, the time of the theft was Sep nineteen, 2017, 15:08. So that means the theft took place before the unknown IP accessed my account — this could only be ane time difference between the app and the IP logger, every bit I know the GateHub team works from Slovenia and and then to the UK there is one hour time difference.
The other odd matter here is the thief got into my business relationship and within 1 minute knew exactly what to practise, he/she accessed my business relationship, exhanged ETH for XRP, and and so transferred XRP out of my account to some other account. All within ane minute? Very strange! Either the person knew how to navigate GateHub (insider?) or a arrangement glitch.
Device Logs:
GateHub also has a device log, and the same accost is on there, merely on a different date, Sep 27, 2017, via Chrome (Windows).
2602:ffc8:1:c:9cbd:c2a6:f420:3bd7 (United states of america IP)
GateHub Email Notification:
GateHub sends emails every time an IP logs into your business relationship they don't recognise. I also got an email on the 24-hour interval the thief accessed my wallet. GateHub notwithstanding immune admission to the thief's IP address (2602:ffc8:1:c:9cbd:c2a6:f420:3bd7) fifty-fifty though I did not "Allow Admission" equally requested by GateHub's email (meet beneath image 8 for e-mail). So why did GateHub allow access to my wallet from an unknown IP address without my approving?

Engaged Cyber Security Professionals (independent of each other):
I got two independent freelance cyber professionals look at my issue. Here are their responses/findings.
Cyber Professional i:
- Because of the method of assail information technology appears the hacker got into the GateHub user interface and so jacked some accounts.
- It could possibly be am ex acquaintance or employee, someone familiar with their systems.
- Information technology's almost impossible to crevice your passwords and snake through brute strength.
- The fashion they accessed it seems like it was routed through back end.
Cyber Professional person 2:
- I'm pretty confident based on what I've seen that your GateHub account was compromised through their web interface and that your network wasn't compromised. It's unfortunately all too common.
- Y'all got an email observe that your account was being accessed past an unknown device (image 8).
- You didn't give it access and in that location are logs showing that information technology was accessed by an unknown VPN.
- Even if they lifted a password by hacking you directly, their security should have stopped any unknown device from accessing your account without your authorisation.
- That email request if you wanted to allow the new device either did not work or was likely spoofed by the hacker exploiting a bug on their site.
Other findings
- During my search on Google, I institute another user who'south XRP was also stolen, by the same address! This person lost 700,000 XRP which in today's value is USD 2.7m! That is an awful lot of money. Since three more user came forward responding to my initial post who lost 20k XRP, 62.5k XRP and 330k XRP respectively. Clearly something is not working with GateHub's systems…
- No doubt the hacker / address that took my crypto is still agile — the total theft can easily go into the millions.
- It appears funds are transferred back and forth between various exchanges and and then the hacker layers the crypto across various addresses with the sole intention to misfile the trail.
Conclusion:
- We know AML/Sanctions regulation exist. So ID&V should have been done via KYC. Surely Changelly and Poloniex know the identities behind the address I mentioned…
- Why did GateHub allow access to my business relationship for an unknown address even though I did non 'Allow Access' on the electronic mail…?
- I do not take a tool / utility to pursue this and 'pull the string' on this ane address (and associated addresses) to see where it ends up, but if my findings are right the web of this criminal operation is HUGE, with many millions at stake, and notwithstanding active as of today (15 December).
- Changelly did not getting back to me about the hacker on their system. So what's next?
Questions from my finish
- Did I interpret the Bithomp activations correctly? (I emailed Bithomp twice now, and sent them a tweet — no reply)
- Why do some Bithomp entries not have names noted, or names next to 'Activated by' noted? How tin can I detect the names? The funds received — is that in Poloniex, or where? See prototype three vs image 6. (I emailed Bithomp twice now, and sent them a tweet — no respond)
Before you go…
If you lot enjoyed this post, please consider showing your back up past clicking on the clapping hands button, likewise as sharing it on your favourite social networks. Don't hesitate to follow me on Medium, Twitter or LinkedIn to stay continued.
Source: https://medium.com/@rhjvr/tracing-my-stolen-funds-stored-without-due-care-by-gatehub-7068c783087c
0 Response to "Currently Unavailable Please Try Again Later Gatehub"
Post a Comment